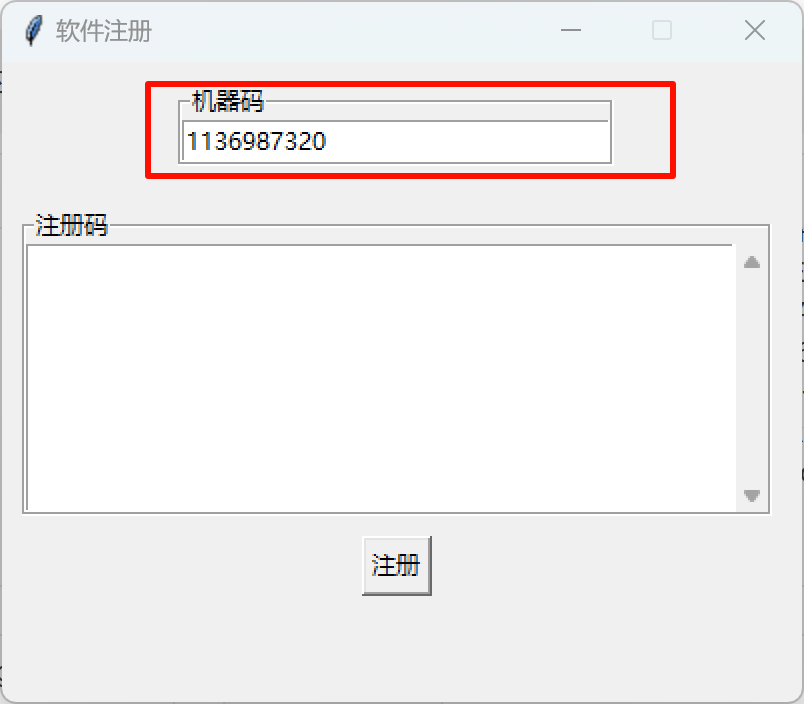
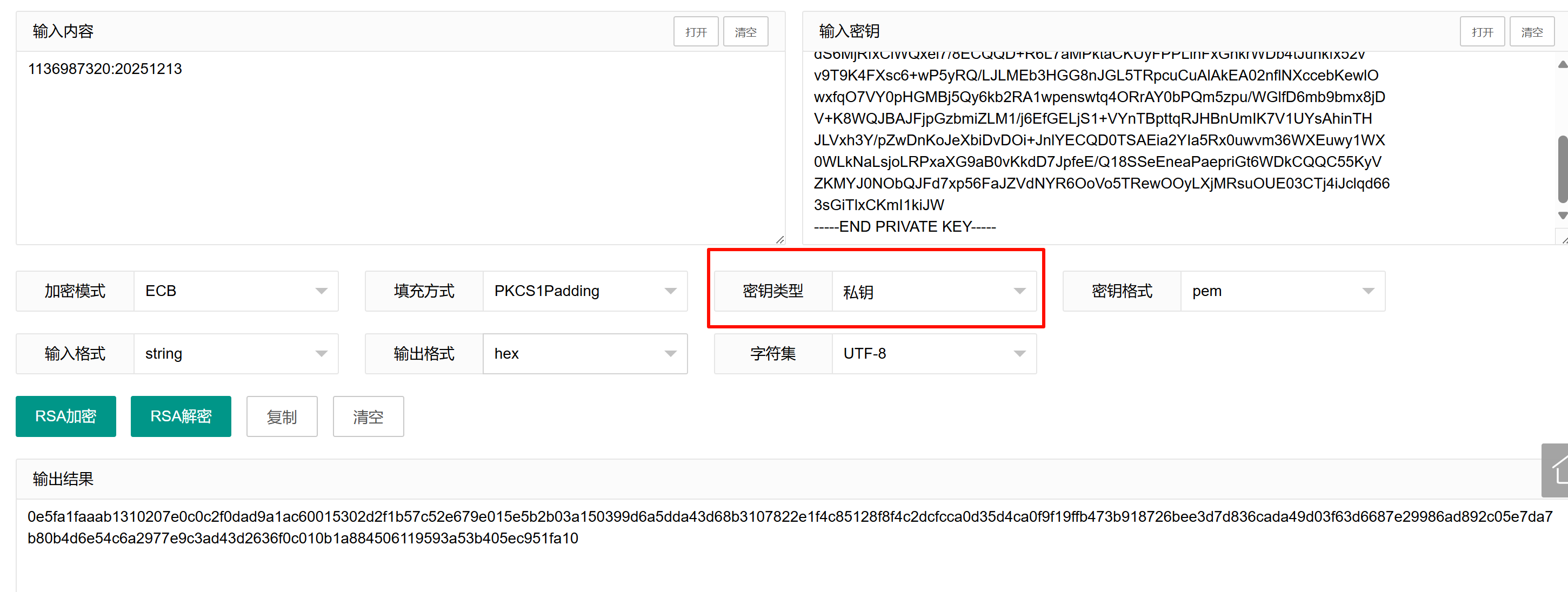
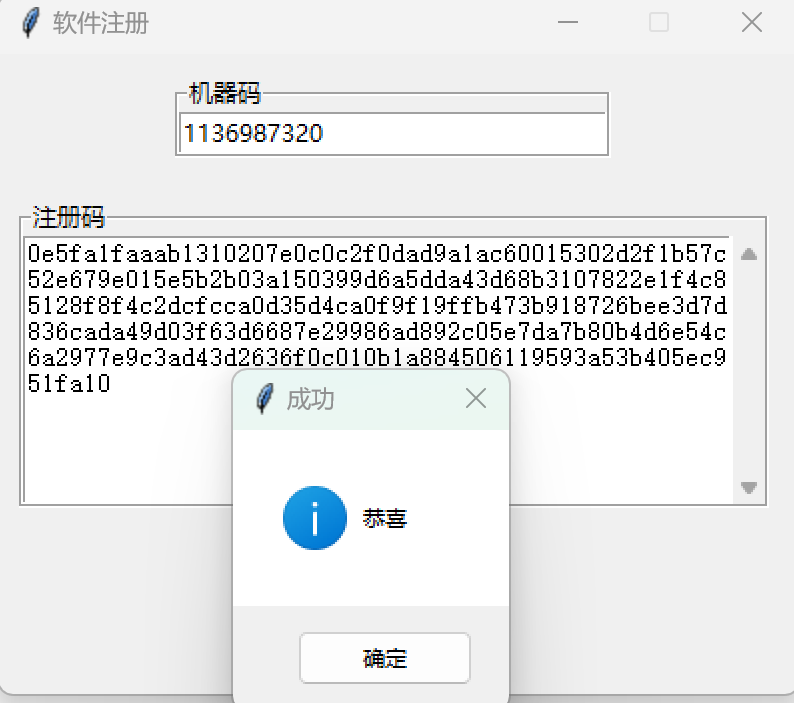
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
| import time
import tkinter
import winreg
from tkinter import END
import M2Crypto
from pyamlboot import sn
REG\_KEY = '\_aml\_s905l3\_sb'
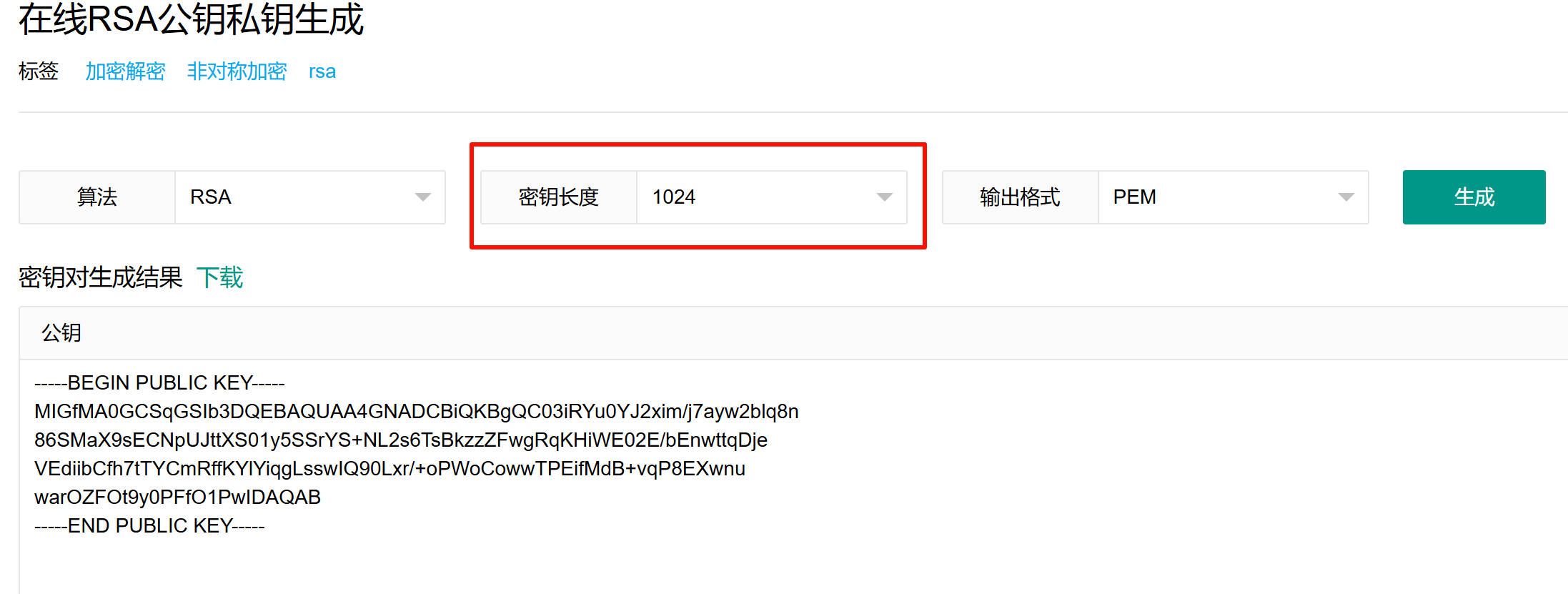
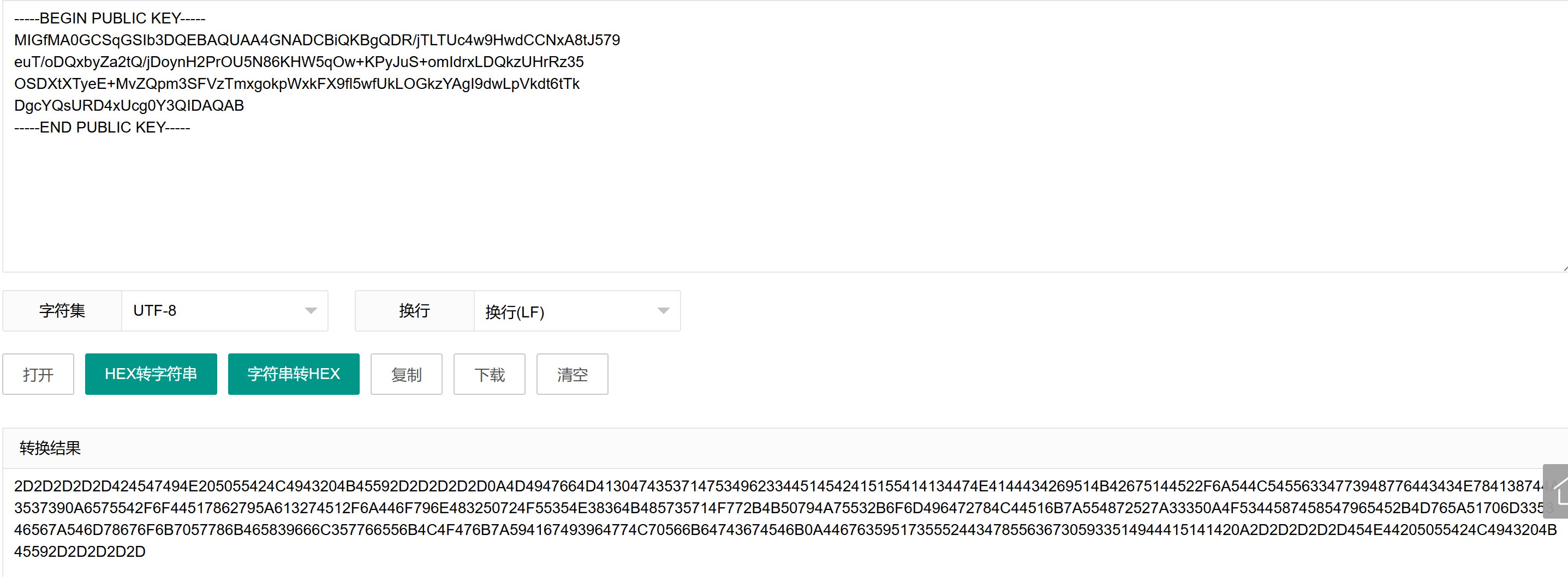
PEM = '2D2D2D2D2D424547494E205055424C4943204B45592D2D2D2D2D0A4D4947664D413047435371475349623344514542415155414134474E4144434269514B42675143564D6C396E635659395A616259496D3862583268756F504F620A4B617950334165704A47355774765A544F6C416F3859304737665A6541693941636A4745696A4A63547A465932773977347033454A5676767939464977744D4A0A3455353157613334647653524F683673356C59574B4F59716A2F74414868624A507650705873612F58416139467A376A7569735769772B52725458564A4A744C0A6C7652514F50444434616B44592B34796F514944415141420A2D2D2D2D2D454E44205055424C4943204B45592D2D2D2D2D'
key\_path = 'SOFTWARE\\\\Software'
def decrypt(msg):
key = bytes.fromhex(PEM)
bio = M2Crypto.BIO.MemoryBuffer(key)
rsa\_pub = M2Crypto.RSA.load\_pub\_key\_bio(bio)
return rsa\_pub.public\_decrypt(msg, M2Crypto.RSA.pkcs1\_padding)
def verify\_reg(code):
try:
if not code: return False
\
plain = decrypt(bytes.fromhex(code)).decode()
\
if ':' not in plain: return False
sn\_part, date\_part = plain.split(':',1)
\
if sn.get\_disk\_info() != sn\_part: return False
\
expire\_date = int(date\_part.replace('-',''))
current\_date = int(time.strftime('%Y%m%d'))
return expire\_date > current\_date
except Exception:
return False
def reg():
import tkinter as tk
ScrolledText = ScrolledText
import tkinter.scrolledtext
root = tk.Tk()
curWidth = 400
curHight = 320
(scn\_w, scn\_h) = root.maxsize()
cen\_x = (scn\_w - curWidth) / 2
cen\_y = (scn\_h - curHight) / 2
size\_xy = '%dx%d+%d+%d' % (curWidth, curHight, cen\_x, cen\_y)
root.geometry(size\_xy)
root.resizable(0, 0)
root.title('软件注册')
label\_frame = tk.LabelFrame(root, '机器码', \*\*('text',))
label\_frame.grid(0, 0, 10, 10, \*\*('row', 'column', 'padx', 'pady'))
\_sn = sn.get\_disk\_info()
isVerify = verify\_reg(verify\_register\_info(REG\_KEY))
machine\_code = tk.StringVar(root, \_sn, \*\*('value',))
entryMachineCode = tk.Entry(label\_frame, machine\_code, 30, \*\*('textvariable', 'width'))
if isVerify:
entryMachineCode.configure('disabled', \*\*('state',))
entryMachineCode.grid(0, 0, \*\*('row', 'column'))
result\_frame = tk.LabelFrame(root, '注册码', \*\*('text',))
result\_frame.grid(1, 0, 10, 10, \*\*('row', 'column', 'padx', 'pady'))
text\_widget = ScrolledText(result\_frame, 50, 10, \*\*('width', 'height'))
if isVerify:
text\_widget.insert(END, '软件已注册')
text\_widget.configure('disable', \*\*('state',))
text\_widget.pack(True, 'both', \*\*('expand', 'fill'))
def callbackMachineCode(event = None):
entryMachineCode.event\_generate('<<Copy>>')
menuPackage = tk.Menu(root, False, \*\*('tearoff',))
menuPackage.add\_command('复制', callbackMachineCode, \*\*('label', 'command'))
def popupMachineCode(event = None):
menuPackage.post(event.x\_root, event.y\_root)
entryMachineCode.bind('<Button-3>', popupMachineCode)
def register():
code\_input = text\_widget.get('1.0', 'end-1c')
isVerify = verify\_reg(code\_input)
if isVerify:
write\_register\_info(REG\_KEY, code\_input)
tk.messagebox.showinfo('成功', '恭喜', \*\*('message',))
root.destroy()
return True
None.messagebox.showinfo('警告!', '不是合法的注册码', \*\*('message',))
return False
button = tk.Button(root, '注册', register, 'disabled' if isVerify else 'active', \*\*('text', 'command', 'state'))
button.grid(2, 0, \*\*('row', 'column'))
root.mainloop()
def isVerify():
if not verify\_reg(verify\_register\_info(REG\_KEY)):
del\_winreg()
return False
return True
def delete\_key\_value():
pass
\
def del\_winreg():
delete\_key\_value()
def write\_register\_info(key, value):
pass
\
def verify\_register\_info(key):
registry\_key = winreg.ConnectRegistry(None, winreg.HKEY\_CURRENT\_USER)
\
|
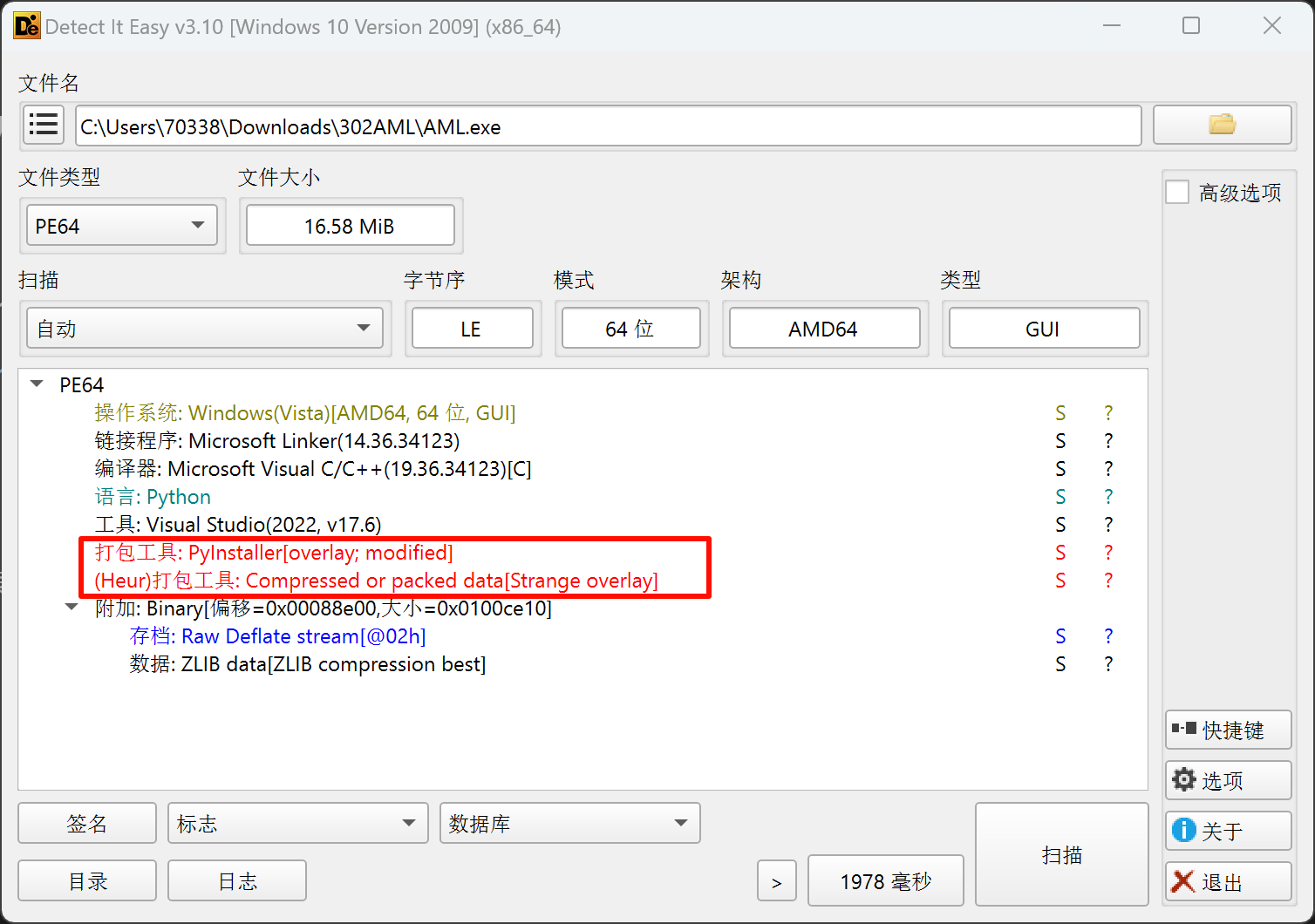 可以看到,程序是使用python编写、PyInstaller打包的
可以看到,程序是使用python编写、PyInstaller打包的

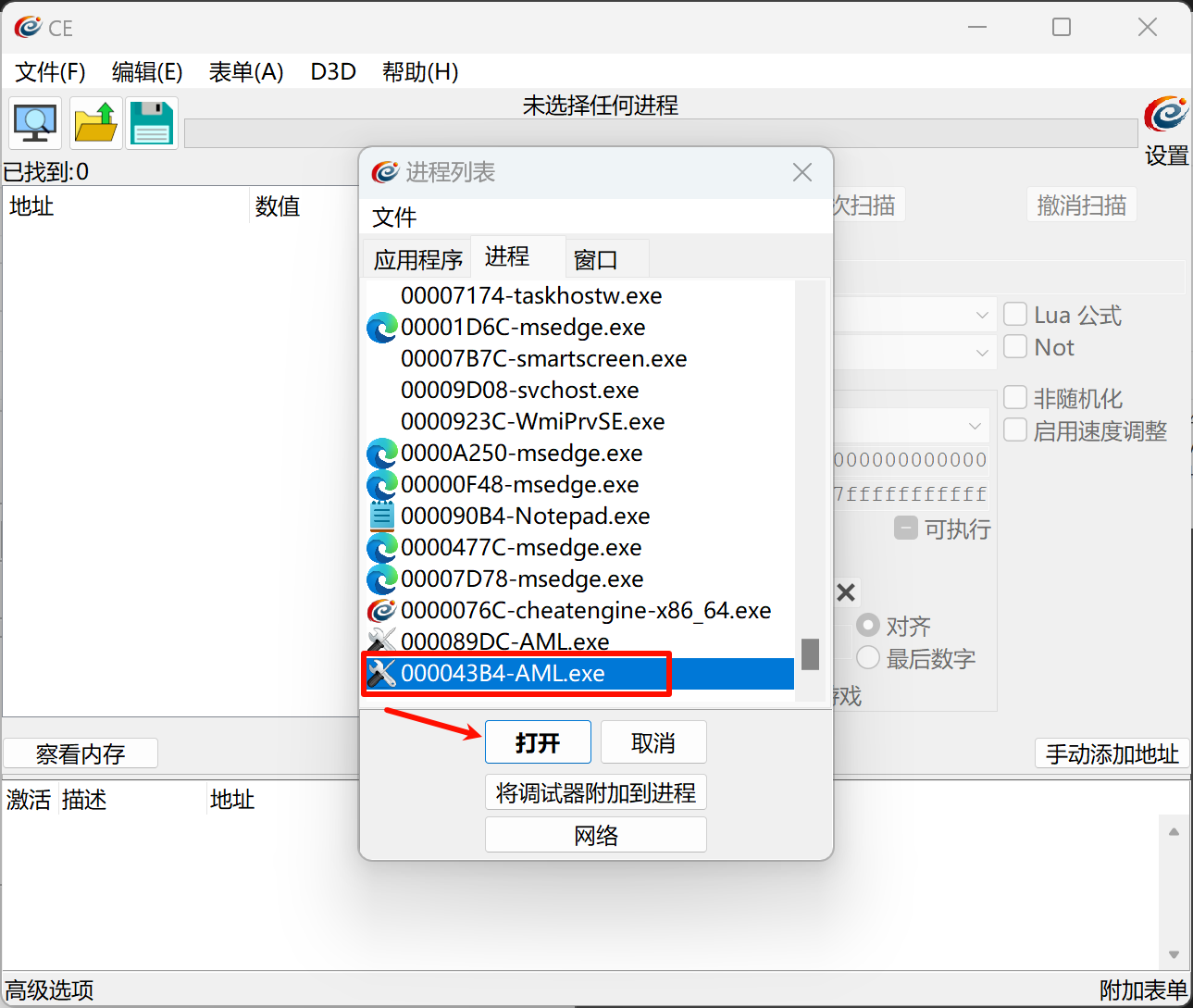
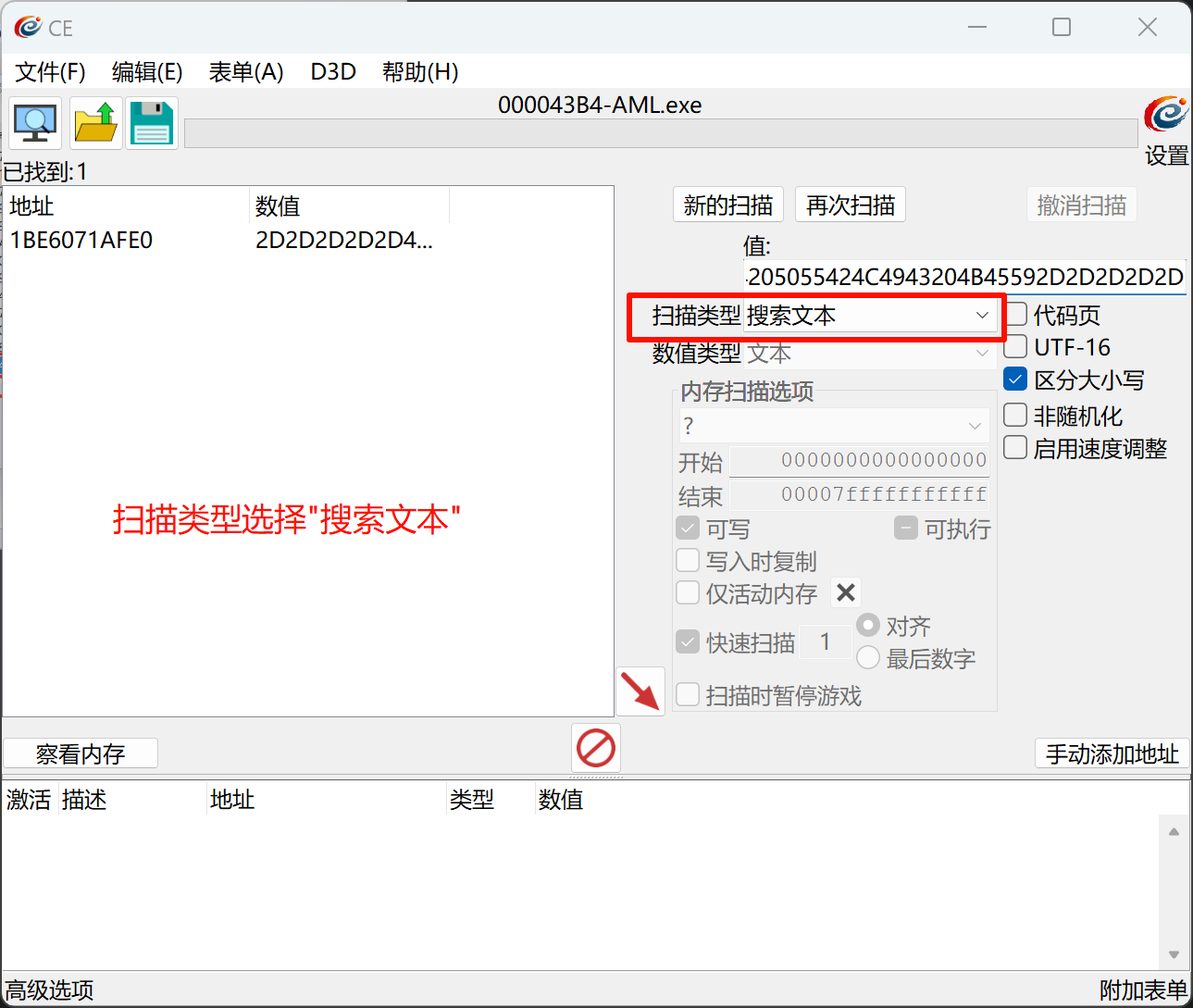
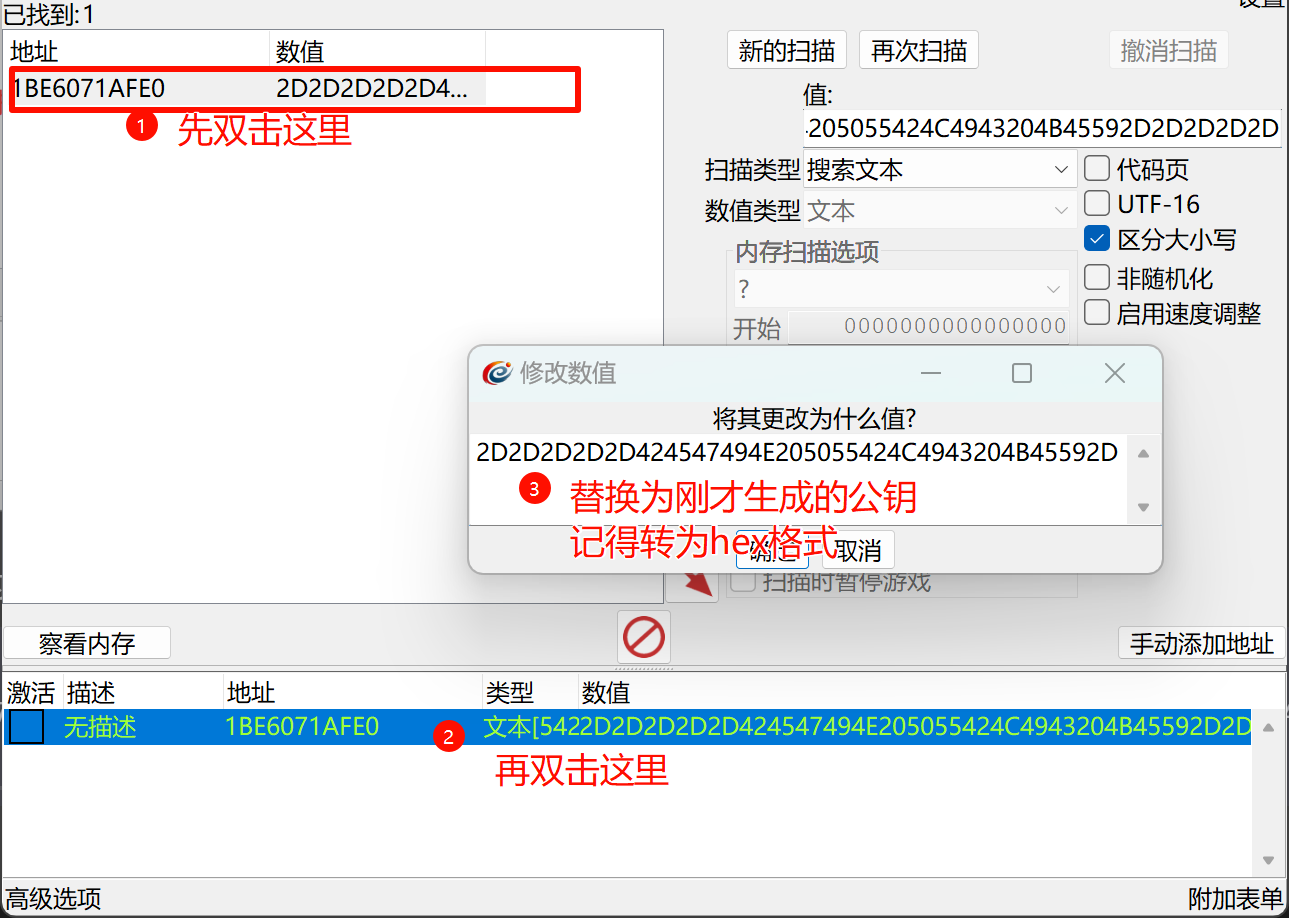 点击确定后就修改成功了
点击确定后就修改成功了